SPR in the cloud
Introduction
This guide will show how to setup virtual SPR and connect to it using a WireGuard VPN client from your phone or desktop computer.
The result is a private VPN with a custom DNS server able to block ads, log traffic, and more.
Quick install
sudo bash -c "$(curl -fsSL https://raw.github.com/spr-networks/super/master/virtual_install.sh)"
Open WireGuard & scan the QR Code/import config - Done!
Virtual SPR Install
What you need
- A linux server running Ubuntu 22.04
- If there is a firewall port 51280/udp needs to be open for incoming traffic
- WireGuard (© Jason A. Donenfeld) installed on your client phone or desktop
Run Virtual Installer
sudo bash -c "$(curl -fsSL https://raw.github.com/spr-networks/super/master/virtual_install.sh)"
What the script does
- downloads the latest SPR repository from https://github.com/spr-networks/super/
- downloads prebuilt docker images
- generate default configs
- setup admin password and auth token for API access
- start SPR
- add a VPN peer and output the WireGuard config
You can also download the script if you want to check it out or add blocklists for ads:
curl -s -O https://raw.githubusercontent.com/spr-networks/super/main/virtual_install.sh
chmod +x virtual_install.sh
sudo DNS_BLOCK=hosts,ads,tracking,redirects ./virtual_install.sh
See here for available blocklists.
Example to block DNS requests to adservers and social media:
sudo DNS_BLOCK=ads,tracking,facebook,tiktok ./virtual_install.sh
If you want to change the admin password you can edit the file configs/base/auth_users.json
Running the script you should see login info, a QR Code & the WireGuard client config. Example:
...
[+] WireGuard config: (save this as wg.conf & import in client)
----------------------------------------------------------
[Interface]
PrivateKey = privkey
Address = 192.168.2.94
DNS = 192.168.2.1
[Peer]
PublicKey = pubkey
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = 198.211.120.224:51280
PersistentKeepalive = 25
PresharedKey = psk
If you want to connect to the VPN using a desktop client, save the config as wg.conf on your local computer.
Configure the VPN client on your device
For iOS and Android
Scan the QR Code in the official WireGuard App (iOS, Android) to import your VPN profile.
Linux, macOS and Windows
Click "Add empty tunnel..." paste the config and set a name for the tunnel. Or, if you saved the config to a file:
- Open your WireGuard client and click "Import tunnel(s) from file"
- Select the wg.conf file
- Click Activate
Admin interface
Make sure you're connected to the VPN endpoint & browse to http://192.168.2.1 to access the admin interface.
Login using the credentials shown in the output from the script or if you set the password manually (NOTE you can check the login info by running SKIP_VPN=1 ./virtual_install.sh).
If you prefer to use curl:
$ export TOKEN="BASE64-TOKEN-FROM-OUTPUT"
$ curl -s -H "Authorization: Bearer $TOKEN" 192.168.2.1/devices
Checkout the documentation to get started using the SPR API.
Modify Blocklists
In the admin interface you can enable more blocklists by clicking Blocklists/Ad-block under DNS:
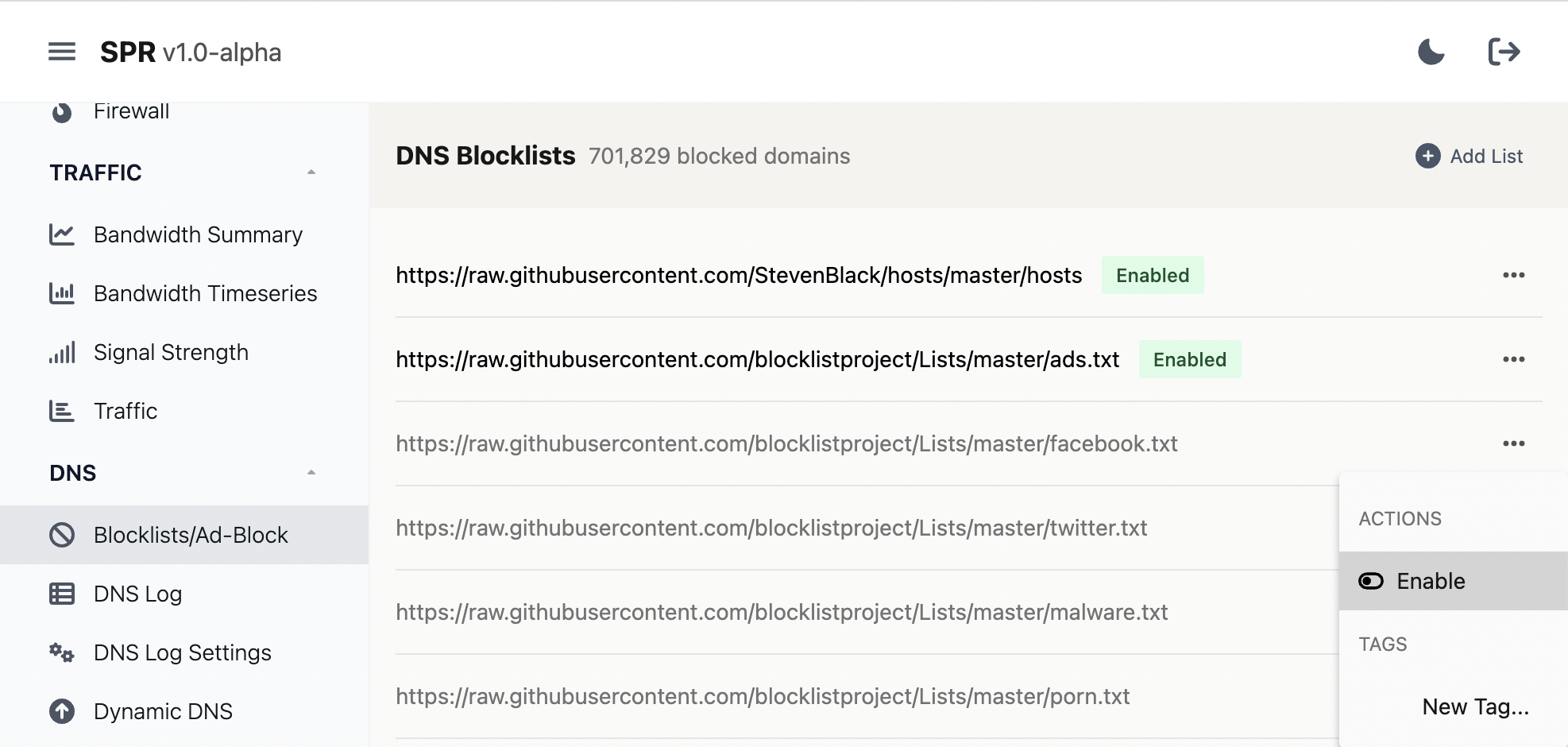
SPR comes bundled with the hosts file from https://github.com/StevenBlack/hosts and the blocklists from the https://github.com/blocklistproject/Lists repository, including: redirect, ads, facebook, twitter, malware, porn, redirect, tracking, youtube, everything
If something is missing you can always add custom blocklists or block specific domains.
View traffic
Navigate to DNS Log in the DNS category, select the client to get a log of domains:
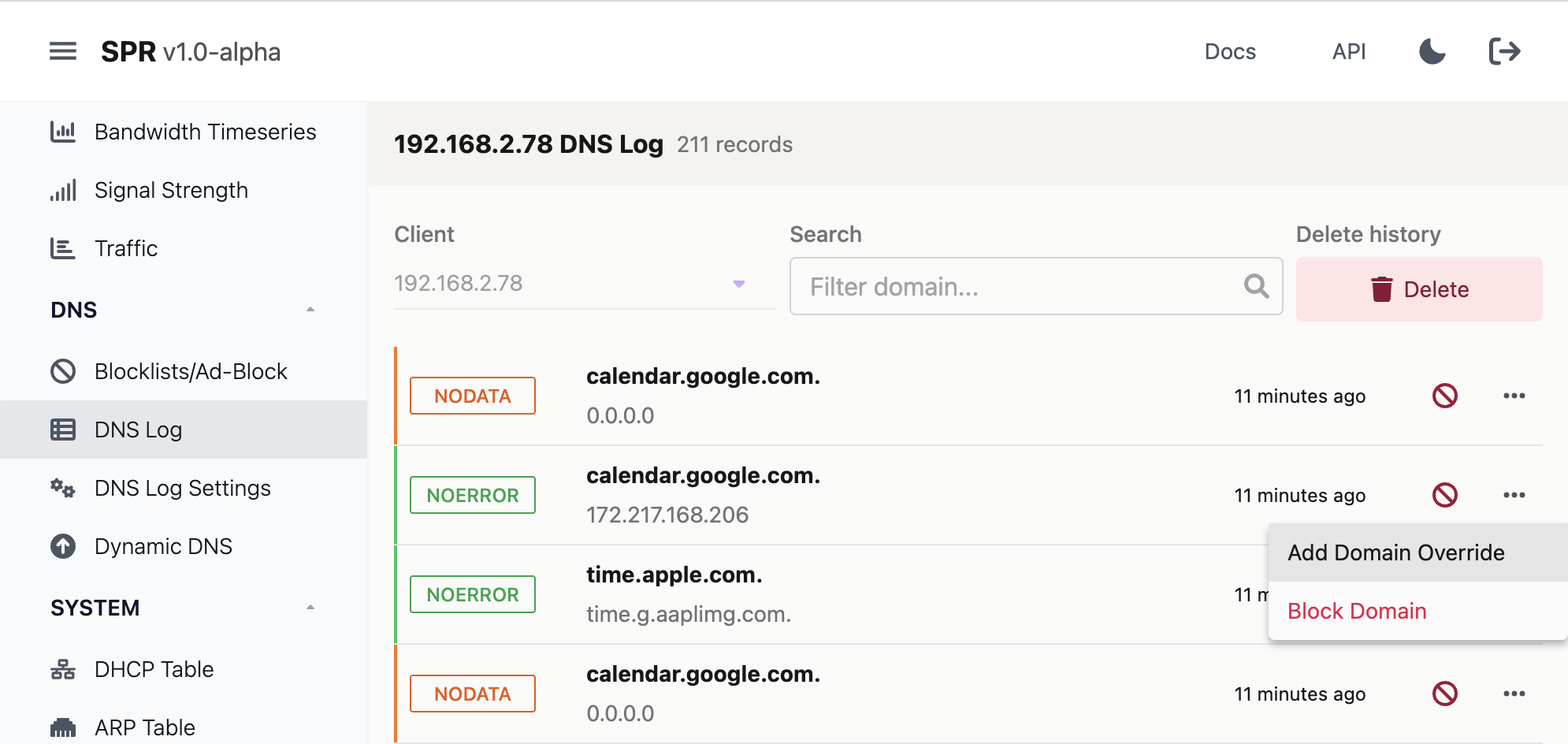
Here you can also add more blocks, domain overrides if you want to allow something temporarily, delete logs or disable them completely under Settings.
It is also possible to get more detail traffic for connections under Traffic:
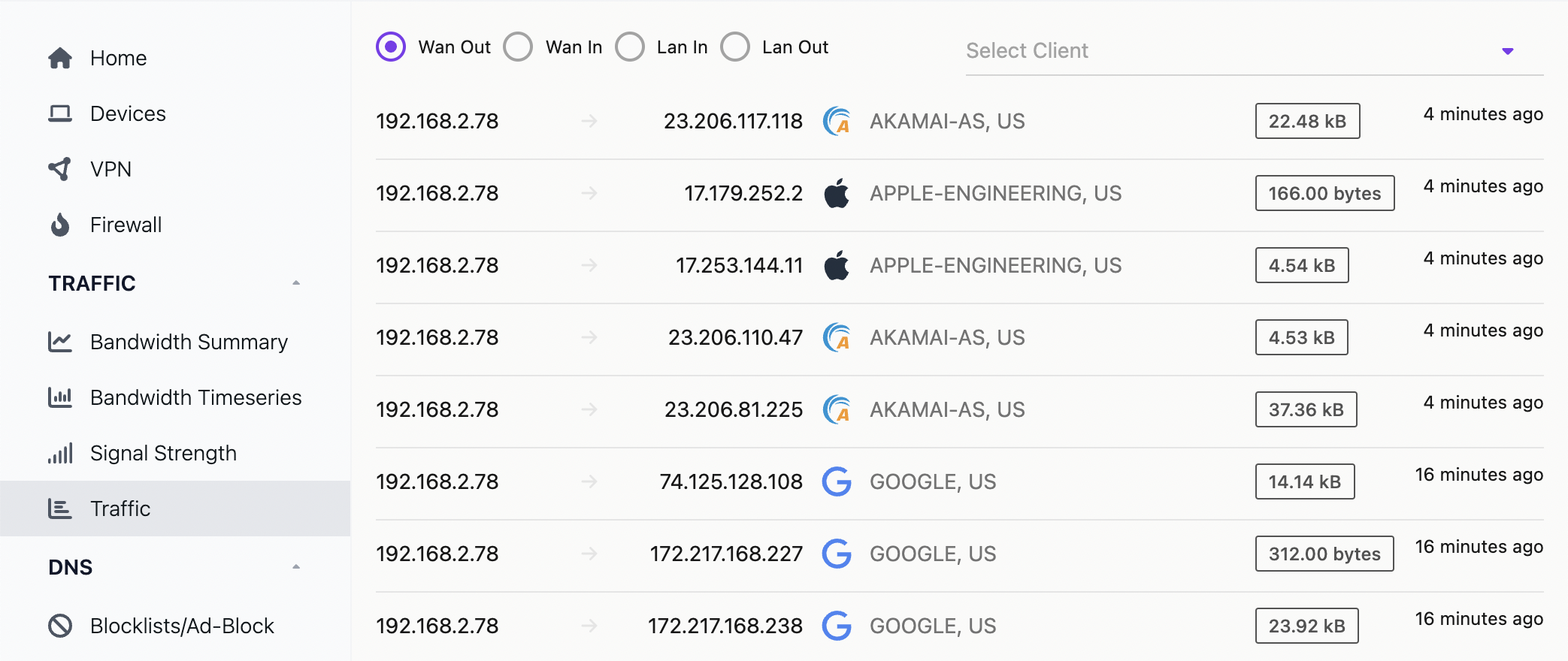
Outro and random notes
You can remove lan from your device groups for a device but its needed to access the admin interface.
SPR is configured to use DNS over HTTPs when resolving domains. You can modify the Coredns configuration under configs/dns/Corefile